Exploring the Wonders of the Night Sky
Overcoming NIST PQC Adoption Challenges with Phio TX and Quantum Xchange
In today’s rapidly evolving cybersecurity landscape, quantum computing represents both a tremendous opportunity and a formidable threat. With advances in quantum computing technology, widely used cryptographic algorithms – such as RSA-2048 – face potential obsolescence. In response, organizations around the world are preparing for a paradigm shift toward post-quantum cryptography (PQC). This long-form technical blog post delves into the challenges for adopting NIST’s PQC standards, examines how Quantum Xchange’s Phio TX solution addresses these hurdles, and provides real-world examples and code samples to help you navigate your organization’s quantum readiness journey.
Table of Contents
- Introduction
- Understanding the PQC Landscape
- Challenges for NIST PQC Adoption
- Quantum Xchange and Phio TX: A Modern Approach
- Real-World Examples and Use Cases
- Technical Implementation: Code Samples and Integration
- Planning Your Transition Strategy
- Conclusion
- References
Introduction
The evolution of quantum computing is undeniable, and its potential to break existing cryptographic standards presents a critical, yet not entirely distant, threat. NIST (National Institute of Standards and Technology) has played a pivotal role in guiding organizations toward adopting post-quantum cryptographic algorithms by outlining the challenges and requirements of a successful migration.
In August 2024, when NIST standardized its first set of quantum-safe algorithms, the urgency to adopt PQC was underscored by three key factors:
- A cryptographically relevant quantum computer (CRQC) may become available sooner than expected.
- Even newly selected cryptographic standards could have vulnerabilities either due to adversarial research or implementation errors.
- “Harvest today, decrypt tomorrow” attacks are already underway, meaning that adversaries are capturing today’s encrypted data with hopes to decrypt it in the quantum future.
This blog post explores how solutions like Phio TX by Quantum Xchange can simplify integration, enhance security, and help organizations incrementally migrate to a quantum-safe environment without undergoing extensive rip-and-replace projects.
Understanding the PQC Landscape
What is Post-Quantum Cryptography?
Post-Quantum Cryptography (PQC) focuses on designing cryptographic systems resilient against the computational power of quantum computers. Unlike quantum encryption methods such as Quantum Key Distribution (QKD), PQC uses mathematical problems believed to be difficult for both classical and quantum computers. The goal is to ensure that even when quantum computers are fully functional, our data remains secure.
PQC algorithms are now being standardized by NIST as part of their effort to create a robust and secure future-proof ecosystem. The PQC movement is not just a theoretical exercise; it is a necessity driven by historical precedents where past cryptographic standards have eventually been compromised.
The NIST PQC Standardization Process
NIST’s multi-year process for standardizing PQC algorithms has been a collaborative, global effort by academics, industry experts, and government bodies. Originally published in the April 2021 report “Getting Ready for Post-Quantum Cryptography,” NIST identified several challenges organizations might face during the cryptographic transition. By August 2024, the first set of quantum-safe algorithms was finalized and released, urging organizations to begin migration immediately, as a full transition is expected to span multiple years.
Key milestones in the process include:
- Evaluation and Selection: Rigorous assessments to identify candidate algorithms based on security, performance, and implementation considerations.
- Standardization: Finalizing the set of algorithms that will serve as the new baseline for quantum-resistant encryption.
- Backup Algorithms: Acknowledging that cryptographic standards evolve and may become vulnerable over time. NIST has already announced backup candidates in anticipation of future vulnerabilities.
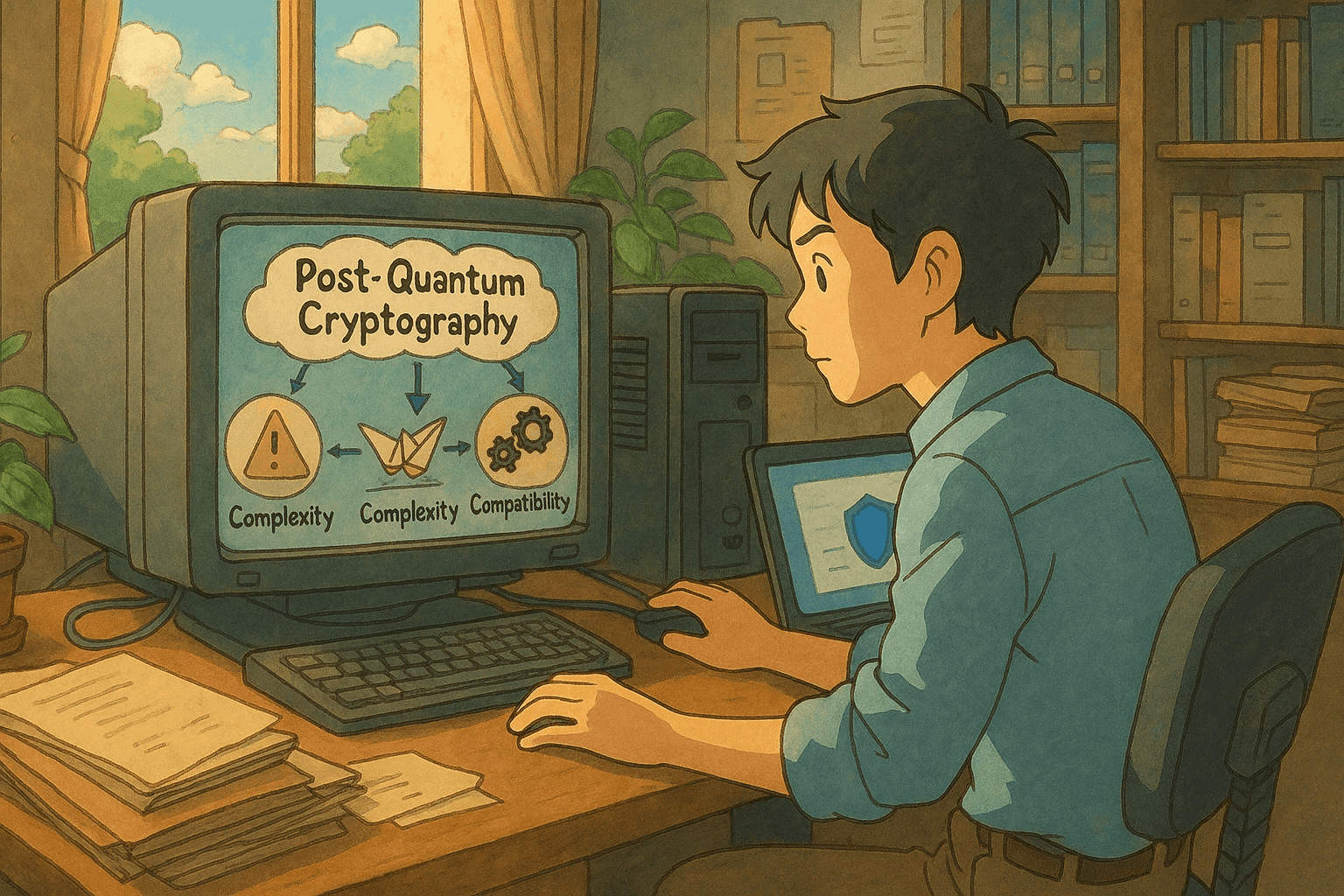
Challenges for NIST PQC Adoption
Transitioning a global digital infrastructure to PQC standards is a herculean task. In this section, we detail the major challenges as outlined by NIST and echoed by industry experts.
Transition Complexity
Changing cryptographic algorithms is inherently disruptive. A successful transition requires modifications across a wide range of systems:
- Software Libraries: Updates are needed in cryptographic libraries and underlying code.
- Hardware Upgrades: Many existing cryptographic solutions are embedded into hardware that may require replacement or rebooting.
- Protocols and Standards: Networking protocols and security standards (SSL/TLS, VPN protocols, etc.) must be revalidated with new algorithms.
- User and Administrative Procedures: Security policies, device configurations, and key management procedures need revision.
Given that past transitions—from DES to AES or from 1024-bit RSA to RSA-2048—took years or even decades, the current transition to PQC is expected to be similarly resource-intensive.
Algorithm Vulnerabilities and Uncertainty
No cryptographic algorithm is forever immune to vulnerabilities. History is rife with examples where widely trusted cryptosystems were eventually compromised due to:
- Mathematical Breakthroughs: New methods in algorithm analysis that reduce the complexity of breaking encryption.
- Implementation Errors: Bugs in the code that lead to exploitable vulnerabilities.
- Side-Channel Attacks: Techniques that exploit physical implementations (timing, power consumption, etc.) rather than flaws in the algorithm.
Even with NIST’s robust standards, there is no absolute guarantee that these algorithms won’t be subjected to future attacks. As such, quantum-ready solutions must offer agility to upgrade or swap out algorithms seamlessly.
“Harvest Today, Decrypt Tomorrow” Attacks
One of the most concerning threats in today’s digital arena is the “harvest today, decrypt tomorrow” strategy adopted by adversaries. Attackers can record encrypted communications now with the expectation that future quantum computers will be capable of decrypting them after algorithms have become obsolete. This scenario is particularly dangerous for sensitive data, as it could lead to a cascade of breaches years after data was initially transmitted.
The threat level is far from hypothetical. The reality is that organizations must protect their data not only from current threats but also from those that might emerge once quantum computing matures. This dual-threat environment creates an urgent need for solutions that provide immediate, incremental quantum resistance.
Quantum Xchange and Phio TX: A Modern Approach
Given the multifaceted challenges associated with PQC adoption, organizations need solutions that are not only secure but also easy to integrate into existing infrastructures. Quantum Xchange’s Phio TX emerges as an innovative solution to navigate these turbulent waters.
Architectural Overview of Phio TX
Phio TX is an advanced key distribution system designed to overlay on your current encryption environment. It is built to be FIPS 203 and 140-3 validated, ensuring compliance with strict cybersecurity standards while offering an immediate boost to your security posture.
Key architectural features include:
- Out-of-Band Symmetric Key Delivery: Phio TX uses a patent-pending system to deliver a supplemental key-encrypting-key (KEK) over a separate communication channel. This means even if an attacker gains access to the primary encryption pathway, they would still need the additional KEK to decrypt the information.
- Crypto Agility: The solution supports all PQC Key Encapsulation Mechanism (KEM) candidate algorithms, allowing organizations to switch between different PQC algorithms without significant re-engineering of their systems.
- Multi-Media Support: Phio TX works over any media capable of transmitting TCP/IP v4 or v6 traffic: fiber optics, copper, satellite, and even 4G/5G networks.
- Scalability and Flexibility: Whether you plan to begin with PQC algorithms and later integrate QKD or opt for a hybrid approach immediately, Phio TX scales along with your security needs.
How Phio TX Addresses Migration Challenges
Phio TX directly tackles the migration challenges posed by NIST’s guidelines while providing several distinct advantages:
- Incremental Transition: Organizations can augment existing cryptographic methods rather than undertaking full-scale replacement projects.
- Enhanced Security Posture: By introducing an additional layer of encryption with KEK, Phio TX significantly mitigates the risk of double compromise, making it exponentially more difficult for adversaries to extract keys.
- Algorithm Agility: With support for various PQC KEM candidates, Phio TX allows organizations to adapt quickly to any future changes in standards or newly discovered vulnerabilities.
- Immediate Deployment: The overlay architecture is designed for seamless integration, making it possible to implement quantum-safe enhancements with minimal operational disruption.
Real-World Examples and Use Cases
The theoretical advantages of any new technology are best understood when illustrated through real-world examples. Here we explore several use cases where Phio TX and Quantum Xchange’s approach have delivered tangible benefits.
Enterprise Key Management Enhancement
Consider a large financial institution that relies on RSA-based Public Key Infrastructure (PKI) for securing digital transactions and protecting customer data. The cryptographic transition challenges in this scenario include:
- Replacing outdated RSA libraries across distributed systems.
- Upgrading hardware security modules (HSMs) to handle new encryption processes.
- Preventing potential “harvest today, decrypt tomorrow” vulnerabilities from being exploited by state-sponsored attackers.
By integrating Phio TX, the institution can overlay its existing encryption environment with a KEK distribution system. The result is immediate strengthening of key management processes as well as a clear migration pathway toward full PQC adoption. Moreover, the inherent agility of Phio TX ensures that even if a future vulnerability is discovered in one algorithm, the underlying infrastructure remains adaptable.
Incremental Adoption with Crypto Agility
A technology company managing a diverse cloud environment might face challenges when multiple legacy systems are involved, each with distinct cryptographic libraries and protocols. Transitioning such a system all-at-once could risk significant downtime or security lapses.
Phio TX offers a solution where the company can incrementally implement quantum-resistant encryption. For example, the IT department can initially roll out Phio TX to secure internal communications and test its integration on a smaller scale. Once validated, the system can be expanded across all platforms automatically, with support for multiple PQC algorithms ensuring that if one algorithm is compromised or becomes obsolete, another can take its place without creating a security gap.
Technical Implementation: Code Samples and Integration
To facilitate the journey toward PQC adoption, let’s delve into some technical aspects of scanning, auditing, and integrating quantum-ready security into your infrastructure. Below are examples of how to use Bash and Python scripts for scanning your current cryptographic setup and parsing the output for further analysis.
Scanning and Auditing Your Current Crypto Infrastructure
Before integrating new quantum-safe solutions, it’s crucial to understand your existing cryptographic environment. The following Bash script leverages the OpenSSL command to scan for supported protocols and ciphers on a given server.
Below is a sample Bash script that scans a host for enabled TLS protocols and ciphers:
#!/bin/bash
# Script: scan_crypto.sh
# Description: Scan a specified host and port for supported TLS protocols and ciphers using OpenSSL.
# Usage: ./scan_crypto.sh <host> <port>
if [ $# -ne 2 ]; then
echo "Usage: $0 <host> <port>"
exit 1
fi
HOST=$1
PORT=$2
echo "Scanning $HOST on port $PORT for supported TLS protocols and ciphers..."
# List supported TLS versions
for TLS_VERSION in tls1 tls1_1 tls1_2 tls1_3; do
echo "----------------------------------"
echo "Checking $TLS_VERSION support:"
openssl s_client -connect ${HOST}:${PORT} -${TLS_VERSION} < /dev/null 2>&1 | grep "Protocol :"
done
# Scan ciphers using the openssl s_client with specific cipher scanning.
echo "----------------------------------"
echo "Scanning for supported ciphers..."
openssl s_client -connect ${HOST}:${PORT} -cipher 'ALL' < /dev/null 2>&1 | grep "Cipher :"
This script demonstrates how to programmatically assess the strength of the cryptographic protocols in use. Such audits are vital before implementing overlay solutions like Phio TX to ensure that the existing infrastructure is adequately mapped.
Parsing Cryptographic Output with Python
After scanning your cryptographic environments, you may wish to parse and analyze the output programmatically. The following Python script shows how to read an output file produced by your scan (e.g., “crypto_scan.txt”) and extract key information:
#!/usr/bin/env python3
"""
Script: parse_crypto.py
Description: Parse OpenSSL scan output to extract supported TLS protocols and ciphers.
Usage: python3 parse_crypto.py crypto_scan.txt
"""
import re
import sys
def parse_scan_output(filename):
protocols = []
ciphers = []
protocol_regex = re.compile(r"Protocol\s+:\s+(.*)")
cipher_regex = re.compile(r"Cipher\s+:\s+(.*)")
with open(filename, 'r') as file:
for line in file:
protocol_match = protocol_regex.search(line)
if protocol_match:
protocols.append(protocol_match.group(1).strip())
cipher_match = cipher_regex.search(line)
if cipher_match:
ciphers.append(cipher_match.group(1).strip())
return protocols, ciphers
def main():
if len(sys.argv) != 2:
print("Usage: python3 parse_crypto.py <scan_output_file>")
sys.exit(1)
filename = sys.argv[1]
protocols, ciphers = parse_scan_output(filename)
print("Supported TLS Protocols:")
for protocol in protocols:
print(f"- {protocol}")
print("\nSupported Ciphers:")
for cipher in ciphers:
print(f"- {cipher}")
if __name__ == "__main__":
main()
This script reads in a file containing the output from the OpenSSL scan and uses regular expressions to extract key protocol and cipher information. By automating such audits, cybersecurity teams can maintain a clear picture of vulnerabilities and plan incremental enhancements with Phio TX.
Planning Your Transition Strategy
Transitioning to a quantum-safe cryptographic infrastructure is a complex, multi-step undertaking. Here, we outline a strategic playbook for organizations beginning their quantum readiness journeys.
Step-by-Step Migration Playbook
-
Initial Assessment and Audit:
- Begin by auditing your existing infrastructure using the aforementioned scripts or similar tools.
- Identify legacy components and outdated cryptographic practices that require immediate attention.
-
Risk Evaluation and Prioritization:
- Conduct a risk analysis focused on key management, data sensitivity, and exposure to “harvest today, decrypt tomorrow” attacks.
- Prioritize systems that handle sensitive data for early PQC adoption.
-
Pilot Integration with Phio TX:
- Deploy a pilot program using Quantum Xchange’s Phio TX solution. Use a sandbox or non-production environment to evaluate integration challenges and performance.
- Leverage Phio TX’s incremental overlay model to supplement, rather than replace, existing encryption without significant disruption.
-
Incremental Rollout:
- Based on pilot results, gradually extend Phio TX to additional environments.
- Maintain crypto agility by deploying support for multiple PQC algorithms. This ensures that your security posture can adapt to emerging quantum threats and evolving NIST standards.
-
Monitoring, Testing, and Compliance:
- Continuously monitor your encryption systems and log performance metrics.
- Implement regular security testing and vulnerability assessments.
- Ensure compliance with relevant standards (e.g., FIPS 140-3, FIPS 203) and document all changes as part of your governance model.
-
Full Migration and Continuous Improvement:
- Once the incremental rollout is complete, begin transitioning systems to rely more heavily on PQC algorithms.
- Integrate monitoring and updating mechanisms to periodically review and update your cryptographic systems based on the latest research and threat intelligence.
Best Practices and Recommendations
- Adopt a Layered Security Approach: Combine Phio TX with traditional encryption for defense-in-depth. This layered architecture minimizes the risk of a single point of failure.
- Stay Agile: The roadmap toward post-quantum readiness is continuously evolving. Ensure that your cryptographic systems are flexible and can accommodate future upgrades.
- Invest in Training: Equip IT and security teams with the latest best practices and insights on PQC. Awareness and preparedness play pivotal roles in mitigating migration risks.
- Engage with Trusted Partners: Collaborate with vendors and technology partners who are well-versed in PQC and quantum-safe security – Quantum Xchange is one such partner offering proven solutions.
Conclusion
As quantum computing edges closer to mainstream viability, the urgency for adopting post-quantum cryptographic measures cannot be overstated. The challenges outlined by NIST—from transition complexity and algorithmic uncertainty to “harvest today, decrypt tomorrow” threats—necessitate a robust, flexible, and forward-thinking approach to cryptographic migration.
Quantum Xchange’s Phio TX provides this solution by offering an overlay architecture that immediately enhances your current encryption systems with quantum-safe key distribution. By facilitating an incremental transition and ensuring crypto agility, Phio TX allows organizations to address contemporary cybersecurity risks while preparing for a quantum future.
For organizations seeking to safeguard their most sensitive data and ensure long-term cryptographic resilience, there’s too much at stake to adopt a “wait and see” approach. Embrace quantum readiness now, implement proven solutions like Phio TX, and stay ahead of emerging threats in today’s dynamic cybersecurity landscape.
References
- National Institute of Standards and Technology (NIST). (2021). Getting Ready for Post-Quantum Cryptography.
- NIST News Releases and Reports on Post-Quantum Cryptography. NIST Post-Quantum Cryptography.
- Quantum Xchange. Quantum Xchange Phio TX.
- FIPS Standards Information. FIPS 140-3 and FIPS 203.
- OpenSSL Documentation. OpenSSL s_client Manual.
By understanding the challenges in NIST PQC adoption and leveraging innovative solutions like Phio TX, organizations can build a resilient infrastructure ready to withstand the quantum threat while preserving and enhancing their current security investments. Stay quantum safe and start your transition today!
Take Your Cybersecurity Career to the Next Level
If you found this content valuable, imagine what you could achieve with our comprehensive 47-week elite training program. Join 1,200+ students who've transformed their careers with Unit 8200 techniques.
