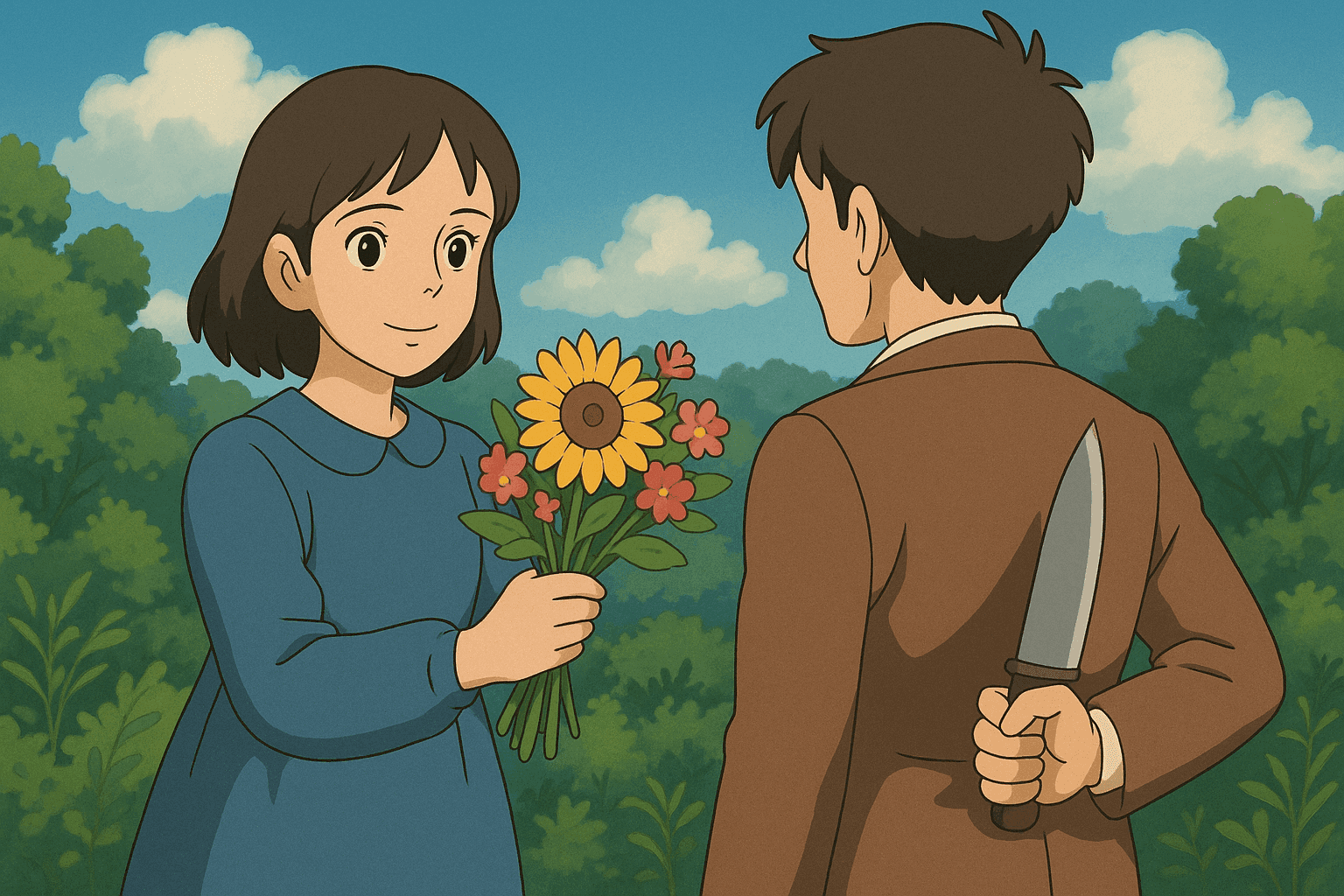
Understanding Weaponized Kindness
What is Weaponized Kindness? An In-Depth Look at Kindness as a Strategic Cybersecurity Tactic
In today’s digital landscape, where social engineering and cyber manipulation are prevalent, a term that is gradually gaining traction is Weaponized Kindness. But what exactly does this term mean, and how can it be used – or misused – within the realm of cybersecurity? In this long-form technical blog post, we will explore the concept of weaponized kindness from its social-psychological origins to its potential applications in cybersecurity. We’ll also dive into real-world examples, provide hands-on technical demonstrations (including Bash and Python code samples), and examine how this emerging idea sits at the intersection of manipulation, digital forensics, and ethical hacking.
Table of Contents
- Introduction
- The Origins of Weaponized Kindness
- Weaponized Kindness in Cybersecurity
- Real-World Examples of Weaponized Kindness
- Technical Implementation and Detection
- Advanced Concepts and Further Applications
- Conclusion
- References
Introduction
The concept of weaponized kindness might at first sound contradictory. How can kindness – a gesture typically associated with benevolence – be weaponized? Yet, in both social and digital settings, even acts of generosity can be harnessed to serve strategic ends. As cybersecurity threats become increasingly sophisticated, adversaries are developing methods that blend genuine-seeming goodwill with manipulative intent.
In this post, we delve into what weaponized kindness entails. We begin by exploring its theoretical underpinnings in social psychology and manipulative altruism, then transition into its practical manifestations in cybersecurity. By taking a holistic look at both the philosophical and technical dimensions of weaponized kindness, you’ll gain a comprehensive understanding of how seemingly benign behavior can mask a more sinister motive.
The Origins of Weaponized Kindness
Social Influence and Persuasion
At its core, Weaponized Kindness involves the strategic use of kind acts to influence behavior, perceptions, and even decision-making processes. Social psychology provides a robust framework for understanding these dynamics. Consider the well-documented principle of reciprocity: when someone offers a kindness, the recipient may feel obligated to reciprocate. This principle has been widely studied by experts such as Robert Cialdini in his seminal work, Influence: Science and Practice.
For example, when an organization offers a small gift or a friendly gesture, it can lower defenses and increase trust—traits often exploited by attackers in social engineering. The use of kindness in such contexts is far from accidental; it is a calculated move designed to establish rapport and induce compliance.
Moral Licensing and Manipulative Altruism
Another key aspect is moral licensing, wherein individuals who have performed good deeds may feel entitled to less ethical behavior subsequently. In a cyber context, this can mean that an actor who cultivates an image of benevolence might later justify more malicious activities. This phenomenon is closely related to the idea of manipulative altruism, where acts of generosity are leveraged to manipulate targets politically, socially, or even digitally.
Scholarly studies have identified these psychological mechanisms as potent tools in both interpersonal dynamics and broader manipulative strategies. Weaponized kindness, thus, raises complex ethical questions. It forces us to consider how our predisposition to trust kindness could be exploited not only in everyday life but also in the sophisticated world of cybersecurity.
Weaponized Kindness in Cybersecurity
Kindness as a Social Engineering Tool
In cybersecurity, trust is both a cornerstone and a vulnerability. Cyber attackers often rely on social engineering techniques to bypass technological security measures. Weaponized kindness is one such technique, wherein an attacker uses seemingly friendly or charitable communications to gain trust and extract sensitive information.
Imagine receiving a heartfelt email from a "trusted" charity asking for a small donation to support a noble cause—and then, more stealthily, requesting sensitive personal or financial information. The recipient, buoyed by the positivity of the outreach, might let their guard down, thereby unwittingly aiding the attacker.
Social Engineering Example: The "Friendly" Phishing Email
Consider a phishing email titled “A Small Act for a Big Change.” The message starts with warm greetings and meaningful appeals to shared values. It might even include detailed bios of supposed team members, pictures of smiling volunteers, and links to fake donation pages. The sender uses kindness as a tool to undermine skepticism and manipulate the target.
Attackers using weaponized kindness know that positive messaging can be disarming. By engaging potential victims with messages that match their desire for social good, these campaigns can achieve higher success rates compared to more traditional, aggressive phishing tactics.
Real-World Examples of Weaponized Kindness
Philanthropic Manipulation in Politics & Business
Weaponized kindness is not a new phenomenon. In politics and business, the concept of strategic philanthropy has been analyzed extensively. Corporations or political figures may perform charitable acts—donating to charity events, participating in community outreach, or even sponsoring local sports—in order to cultivate a positive public image. When such acts are used to shield unethical practices or to gain unwarranted influence, they illustrate weaponized kindness in a tangible way.
For instance, consider a large corporation that sponsors a popular community event with favorable media coverage. In the background, however, that same corporation might be engaging in questionable business practices. Here, the benevolent image is weaponized to mask underlying exploitation or malfeasance.
Cyber Tactics: Crafting Trust and Bypassing Security
In the digital realm, advanced persistent threat (APT) groups have been observed leveraging weaponized kindness as part of their reconnaissance and attack strategies. An attacker might begin by offering free cybersecurity advice, or share a seemingly benign tool that purports to help with system optimization. Once trust is built, the actor may incorporate code that subtly installs a backdoor, all under the guise of providing a helpful service.
Another instance is the use of “gift” software download campaigns. A free, open-source tool is released that promises to simplify tasks like email management or network scanning. The tool is widely publicized using channels known for technology tutorials and acts of goodwill. However, hidden within the code are subtle modifications that allow adversaries to monitor user activity or exfiltrate confidential data. These examples underscore the dual-edged sword of weaponized kindness: what appears to be a benefit can quickly become a critical vulnerability.
Technical Implementation and Detection
Understanding weaponized kindness in theory is one thing—but detecting and mitigating it in practice is complex. In this section, we’ll explore technical methods to identify potential instances of weaponized kindness in cybersecurity. We’ll provide example code in Bash and Python, demonstrating how to scan logs, parse network traffic, and detect suspicious patterns that might indicate manipulative behavior.
Scanning for Weaponized Kindness Activity
Before diving into the code, it’s crucial to outline what technical indicators might suggest that weaponized kindness is at work. Some red flags include:
- Inconsistent Messaging: Communication channels that display an overly positive or charitable tone may hide ulterior motives.
- Anomalous Network Traffic: Unexpected outbound connections following what appear to be benign software downloads.
- Behavioral Anomalies: Users or systems suddenly displaying unusual activities after interacting with “friendly” software or communications.
By establishing baseline metrics for system behavior and monitoring for deviations, cybersecurity professionals can begin to detect these red flags early in an attack.
Parsing Suspicious Logs using Bash
Let’s start with a simple Bash script to scan and parse system logs for suspicious patterns that might indicate weaponized kindness tactics. For instance, if you’re monitoring your web server or application logs, you want to flag entries containing overly “friendly” keyword patterns or unexpected parameters suggesting data exfiltration.
Below is a sample Bash script that scans Apache logs for suspicious keywords that might be associated with weaponized kindness:
#!/bin/bash
# scan_logs.sh
# This script scans Apache access logs for suspicious keywords associated with weaponized kindness
LOG_FILE="/var/log/apache2/access.log"
OUTPUT_FILE="suspicious_entries.txt"
# Define an array of suspicious keywords
keywords=("kindness" "charity" "donation" "helpful" "free gift" "community support" "noble" "generosity")
# Clear the output file if it exists
> "$OUTPUT_FILE"
# Scan the log and output lines that contain any of the keywords
for keyword in "${keywords[@]}"; do
echo "Searching for keyword: $keyword"
grep -i "$keyword" "$LOG_FILE" >> "$OUTPUT_FILE"
done
echo "Suspicious log entries have been saved to $OUTPUT_FILE"
How the Bash Script Works
- The script defines the log file location and an output file for suspicious entries.
- A list of suspicious keywords is declared. These keywords might be associated with communications or download campaigns that use weaponized kindness as a lure.
- For each keyword, the script uses
grepto find matches in the log file, appending any matching lines to the output file. - After running the script, any log entries containing these keywords are flagged for further investigation.
This script is a simplistic demonstration. In a real-world scenario, you’d likely integrate more sophisticated log analysis tools, correlate with other indicators of compromise (IoCs), and perhaps use a SIEM (Security Information and Event Management) system for enhanced monitoring.
Python – Analyzing Network Traffic for Manipulative Patterns
Python is immensely powerful for network traffic analysis. In situations where network logs or packet captures (PCAPs) suggest abnormal communication patterns following "kindness" campaigns, you can use Python libraries such as Scapy or Pandas to parse and analyze the data.
Below is an example Python script that uses the scapy library to filter network traffic and detect anomalies such as unexpected external connections after a download event.
#!/usr/bin/env python3
"""
analyze_traffic.py: Analyze pcap files to detect suspicious activity that could indicate weaponized kindness
Usage: python3 analyze_traffic.py traffic_capture.pcap
"""
import sys
from scapy.all import rdpcap, IP
def filter_packets(packets):
"""
Filter packets that are suspicious based on certain criteria.
For instance, we expect that after a benign download, there might be unexpected outbound IP connections.
"""
suspicious_packets = []
for packet in packets:
if packet.haslayer(IP):
ip_layer = packet.getlayer(IP)
# Example logic: Flag traffic with non-standard ports or unexpected IPs
# For demonstration, we flag external connections (destination not in local network range)
# Adjust the local network as per your configuration. Here, we assume 192.168.x.x.
if not ip_layer.dst.startswith("192.168."):
suspicious_packets.append(packet)
return suspicious_packets
def main(pcap_file):
print(f"Loading packets from {pcap_file}...")
packets = rdpcap(pcap_file)
print(f"Total packets loaded: {len(packets)}")
suspicious_packets = filter_packets(packets)
print(f"Number of suspicious packets detected: {len(suspicious_packets)}")
# Optional: Save suspicious packets to a new pcap file or output details
with open("suspicious_packets.txt", "w") as f:
for pkt in suspicious_packets:
f.write(f"{pkt.summary()}\n")
print("Suspicious packet details have been saved to suspicious_packets.txt")
if __name__ == "__main__":
if len(sys.argv) != 2:
print("Usage: python3 analyze_traffic.py <pcap_file>")
sys.exit(1)
main(sys.argv[1])
Explaining the Python Script
-
Library Import and PCAP Processing:
The script starts by importing Scapy’s functionalities and reading a PCAP file supplied as a command-line argument. This PCAP file represents captured network traffic. -
Filtering Packets:
The functionfilter_packetsiterates through the network packets. In our example, we filter for packets that indicate connections to external IP addresses (i.e., not within the typical local network range, here assumed to start with “192.168.”). This is a rudimentary screening method intended for demonstration. -
Output and Reporting:
The script prints the number of suspicious packets and then saves a summary of each packet to a text file for future review.
The Python script serves as a fundamental example of how to use automation to scan for suspicious network activity that might coincide with weaponized kindness tactics. In practice, you would refine the filtering criteria further—possibly integrating IP reputation databases and correlating with known IoCs to accurately pinpoint malicious activity linked to social engineering or disguised outbound data transfers.
Advanced Concepts and Further Applications
Weaponized kindness in cybersecurity isn’t confined solely to phishing emails or data exfiltration. Its broader applications can have subtle yet pervasive effects in the domain of network security and digital communications.
Behavioral Analytics Integration
Modern security systems increasingly rely on behavioral analytics. By incorporating machine learning algorithms to learn baseline user behavior, analysts can identify deviations that signal potential weaponized kindness attempts. For example:
- User Behavior Analysis (UBA): Establish profiles of normal user activity, and automatically flag anomalous activities (e.g., an unusually large download following a benevolent-looking email).
- Anomaly Detection: Use statistical models to flag communication patterns that deviate from established norms. Such models might consider frequency, duration, and context of network connections.
- Sentiment Analysis: Combine natural language processing (NLP) techniques with network log analysis to evaluate the sentiment of incoming communication. A sudden surge in overly positive messaging from a relatively unknown source might warrant further investigation.
These advanced techniques require comprehensive data collection, robust statistical analysis, and, often, integration with existing SIEM platforms. However, the evolving threat landscape demands such innovations to counter increasingly sophisticated attacks that employ the guise of benevolence.
The Future of Weaponized Kindness in Cyber Defense
As cybersecurity defenders continue to grapple with ever-evolving threats, the concept of weaponized kindness is likely to become more relevant. Future trends might include:
- Enhanced Deception Tactics: Just as attackers use weaponized kindness to fool victims, cybersecurity teams might deploy “counter-kindness” tactics. For instance, decoy systems and honeypots can be designed to offer an appealing, benign interface that lures attackers into leaving traces of their methodologies.
- Automated Threat Hunting: The integration of AI and machine learning in threat hunting will enable real-time detection of anomalous behavior patterns. By training models to identify the subtle indicators of weaponized kindness tactics, organizations can quickly isolate and mitigate potential threats.
- Ethical Considerations and Policy Making: As the practice of weaponizing kindness becomes increasingly recognized, ethical and regulatory frameworks may evolve. Policymakers and industry leaders will need to consider how to distinguish genuinely benevolent actions from strategically manipulative ones, especially in politically and socially sensitive contexts.
Understanding and adapting to these trends is critical. Organizations that proactively refine their cybersecurity posture to counter both traditional and non-traditional exploitation methods will be better prepared to handle the evolving threat landscape.
Conclusion
Weaponized kindness is a multifaceted concept bridging psychology, social engineering, and cybersecurity. What starts as a seemingly benign act of generosity can quickly be transformed into a strategic tool for manipulation and control—both in the physical world and the digital realm. Whether it’s a mimicry of charitable communication in phishing campaigns or the strategic use of benevolent imagery in corporate image management, weaponized kindness challenges our assumptions about trust and morality.
In this post, we’ve examined the theoretical underpinnings of weaponized kindness, looked at how kindness can be weaponized in cybersecurity, and demonstrated practical detection techniques using Bash and Python. We’ve also explored advanced analytical approaches and discussed future trends in the evolution of these tactics.
As we navigate a world where digital and human behaviors are increasingly intertwined, the need for sophisticated threat detection—and the ability to distinguish genuine goodwill from its more insidious, weaponized form—has never been more critical.
By staying informed, employing robust analytics, and continuously refining cybersecurity practices, defenders can mitigate the threats posed by weaponized kindness. Ultimately, understanding these dual-use tactics can empower professionals to build a safer digital ecosystem while preserving the fundamental human values of kindness and compassion.
References
- Cialdini, R. B. (2001). Influence: Science and Practice
- Merritt, A. C., Effron, D. A., & Monin, B. (2010). Moral self-licensing: When being good frees us to be bad. Social and Personality Psychology Compass
- Baur, D., & Schmitz, H. P. (2012). Corporations and NGOs: When Accountability Leads to Co-optation. Journal of Business Ethics
- Marquis, C., & Qian, C. (2014). Corporate Social Responsibility Reporting in China: Symbol or Substance? Organization Science
- De Freitas, J., & Cikara, M. (2018). The persuasiveness of manipulative altruism in promoting unpopular causes. Journal of Experimental Psychology: General
By understanding both the human psychology behind acts of kindness and the ways these acts can be weaponized, cybersecurity professionals can remain one step ahead in the eternal game of trust versus exploitation. Stay vigilant, implement robust detection strategies, and remember: even acts of generosity should be examined with a critical eye in the high-stakes world of cybersecurity.
Feel free to share your thoughts in the comments, subscribe for more technical insights, or reach out with your questions about weaponized kindness and cybersecurity. Stay kind, stay informed, and code securely!
Take Your Cybersecurity Career to the Next Level
If you found this content valuable, imagine what you could achieve with our comprehensive 47-week elite training program. Join 1,200+ students who've transformed their careers with Unit 8200 techniques.
